Incorporating Digital Security into Your Field Service Business
- September 25, 2019
- By: Vonigo

In the 21st Century, digital security is a key part of your field service business. Parts of the field service industry have been slow to adapt to the online revolution. A strong web presence and investment in technology are mandatory today. That means paying attention to digital security as well.
Whether your business focus is moving, cleaning, junk removal, or what-have-you, integrating digital security principles into your field service business will improve the experience for your customers and employees. It can also make you more money in the long run.
Those that work in the field, outside of an office, present a special challenge when it comes to cybersecurity. The mobile hardware and software they use need to be protected from the same types of threats found in the office. It also needs to stand up to travel and the elements, spotty connectivity, and unpredictable circumstances on job sites.
Let’s examine modern digital security for a field service business. We will use the lens of best practices and common mistakes found in the field.
Hardware Options for Field Service
Office workers typically complete most of their day job from a desktop or laptop computer. Field service workers need to be more agile and mobile. Equip them with a smartphone or tablet, loaded with the software and apps needed to connect to the company’s systems.
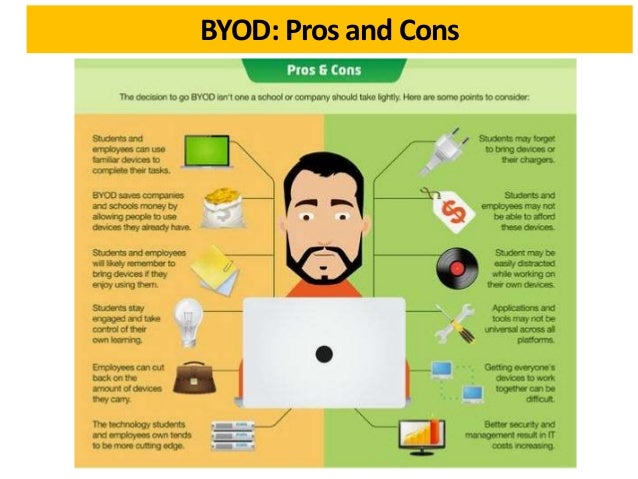
But corporate leadership has a very important decision to make when it comes to mobile hardware. They can choose to procure devices through the company. Alternately, they can let employees use their own equipment, referred to as bring your own device (BYOD).
There are benefits and risks for each option. Procuring dedicated hardware can be costly, but those devices remain fully under company control and are easier to secure. BYOD programs create more potential for security problems and compatibility but reduce the purchasing obligation for the company. On the other hand, new hires may not own such devices, and may not be able to easily afford them.
Hacking Wearable IoT Devices

The Internet of Things (IoT) is a broad term that covers all types of smart devices that connect to the internet through wireless technology. In the home, things like smart light bulbs and smart coffee makers are making life easier for consumers. A subsection, the IIoT (Industrial Internet of Things), has found itself probed mercilessly by hackers looking for a security vulnerability.
More field service companies now equip their staff with wearable devices. These devices track and measure activities in real-time, rather than having to rely on manual input like timesheets. But while the IoT can simplify operations, these devices come with certain digital security risks that can’t be ignored.
Hackers now target IoT wearables because they tend to run on very basic operating systems. They have little in the way of security protection built-in. In addition, these smart devices constantly transmit data over a wireless frequency. If a hacker can compromise a device or intercept its traffic, then they could cause a huge data breach in your systems.
Staying Secure on Public Wi-Fi
As mentioned, the hardware that field service technicians use is reliant on consistent network connectivity. Using free public wi-fi networks may be tempting but should be done very carefully. Otherwise, hackers will be able to deploy any of a number of cyberattacks. They can then steal data right from your smart devices.
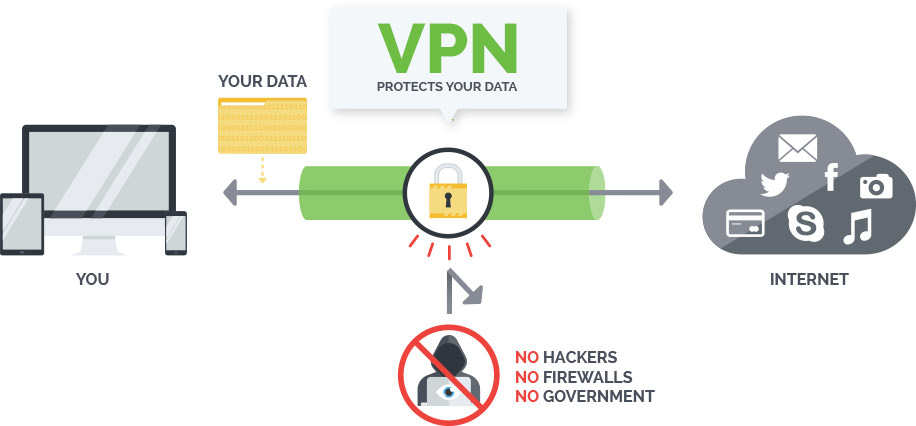
Install a virtual private network (VPN) client or program on every phone and tablet. While there are literally hundreds of VPNs to choose from, comparison reviews let you narrow the field quickly. Look for specific security features offered by top providers like NordVPN. One example: a kill switch. It cuts the internet connection if it detects that the VPN is leaking data or not functioning properly.
With a VPN activated, all outgoing data is encrypted before it leaves your device. The traffic is linked to a different, anonymous IP address. Even if a hacker infiltrates the network, they will not be able to decode the data you transmit.

SaaS Could Shift Digital Security Responsibility Away from Your Field Service Business
To digitally secure your field service business, you must look at the rise of Software as a Service or SaaS. This subset of cloud computing is the fastest-growing area and features a shift from buying software to subscribing to it. This shifts major chunks of responsibility for securing separate elements of the computing environment to the software lessor.
This is something to keep in mind before you lay out big chunks of cash for an installable CD-Rom. Those days have sort of passed us by. The best way to find lockdown cybersecurity might be to pass the job off to someone else. Vonigo’s field service management software is cloud-based, secure, and comes with uptime guarantees that will help you securely manage your field service business.

Investing in Biometrics
Up to this point, we’ve focused primarily on software-related security threats. In those, the hacker looks to infiltrate your systems through a network-layer attack. However, some cybercriminals will try to take control of a device through direct contact.
Given how much data field service technicians interact with, their phones and tablets serve as portals that could become vulnerable. Imagine if a phone was lost and left unlocked for anyone to view its contents. The ramifications could be disastrous. Digital security for a field service company needs to be both physical and virtual.
That’s why field service organizations need to take extra steps to ensure the physical security of their digital devices. Biometrics plays a key role in this because the capabilities are far more secure than a traditional username and password. These days you can restrict devices for free using fingerprint scanning or even facial recognition. It takes a few moments to set up, but the peace of mind is worth the investment.
Responding to an Incident
Training is critical when comes to ensuring the security of your company and its hardware and software. Field service technicians should learn about the different cyber threats to watch out for when working remotely. Make sure to place extra emphasis on the need to report any lost devices or other tech issues.
When an incident is reported by an employee, the IT team should have a clear plan of how to react. Assuming they have remote access to all field devices, those affected should be isolated and disconnected from all wireless protocols. This will help to limit the spread of the cyberattack and preserve the data assets located on servers.
Final Thoughts on Digital Security for a Field Service Business
The fast evolution of technology has dramatically changed how companies run their field service and support operations. Employees can stay connected to the main office at all times through digital devices. This makes the entire workflow more efficient and customer friendly.
But every new piece of hardware or software that is added to a company’s network creates a greater cyber-attack risk. Hackers hunt for organizations with inadequate security policies and then plan different schemes to take advantage of their vulnerabilities. Craft a strong digital security strategy for all your field service business’s devices and use secure, cloud-based field service software. That way you can keep field service technicians from being a security vulnerability as they go about their workday.
Want to learn about how cloud-based field service management software can help you manage the growth and digital security of your business? Book a free, private demo of Vonigo.